Tools and templates for IT teams
Resources for IT assessments, IT strategy, and more
Last updated: May 2025
Today's IT teams are solution-driven. You deliver technology and services that meet current business needs and scale for the future. You support business growth — all while maintaining day-to-day support.
With all of this responsibility, IT teams have to work efficiently to solve problems and plan new initiatives. It helps to have a few tools handy to jump-start your thinking.
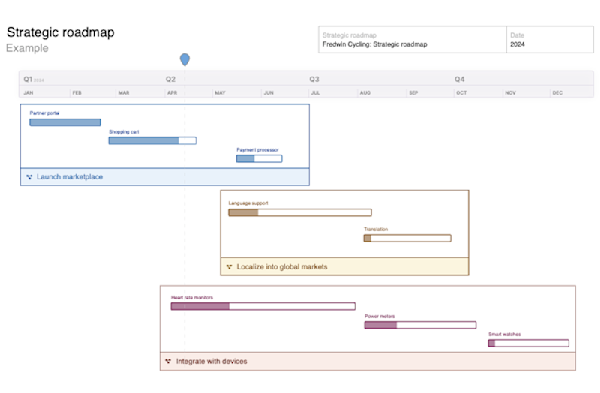
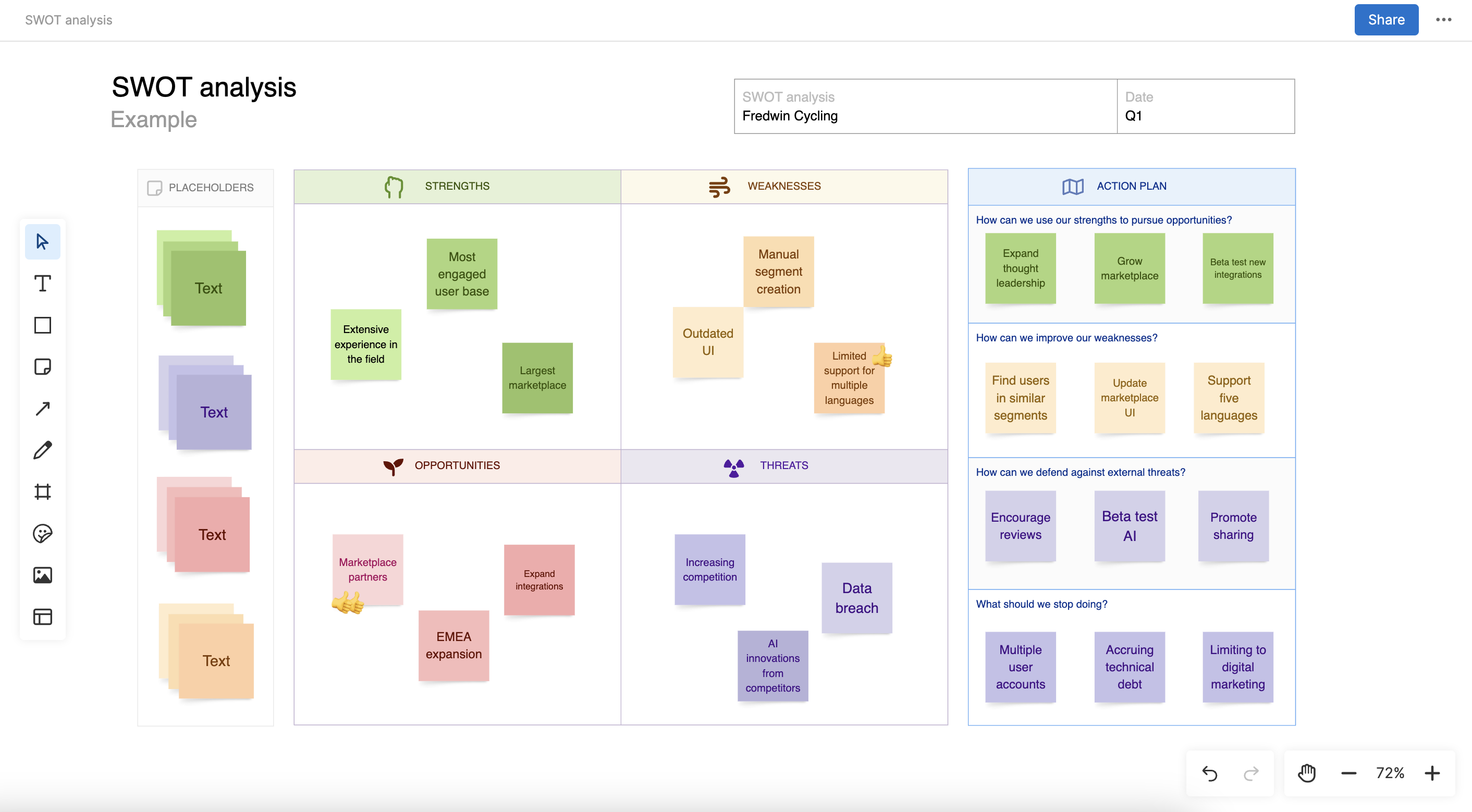
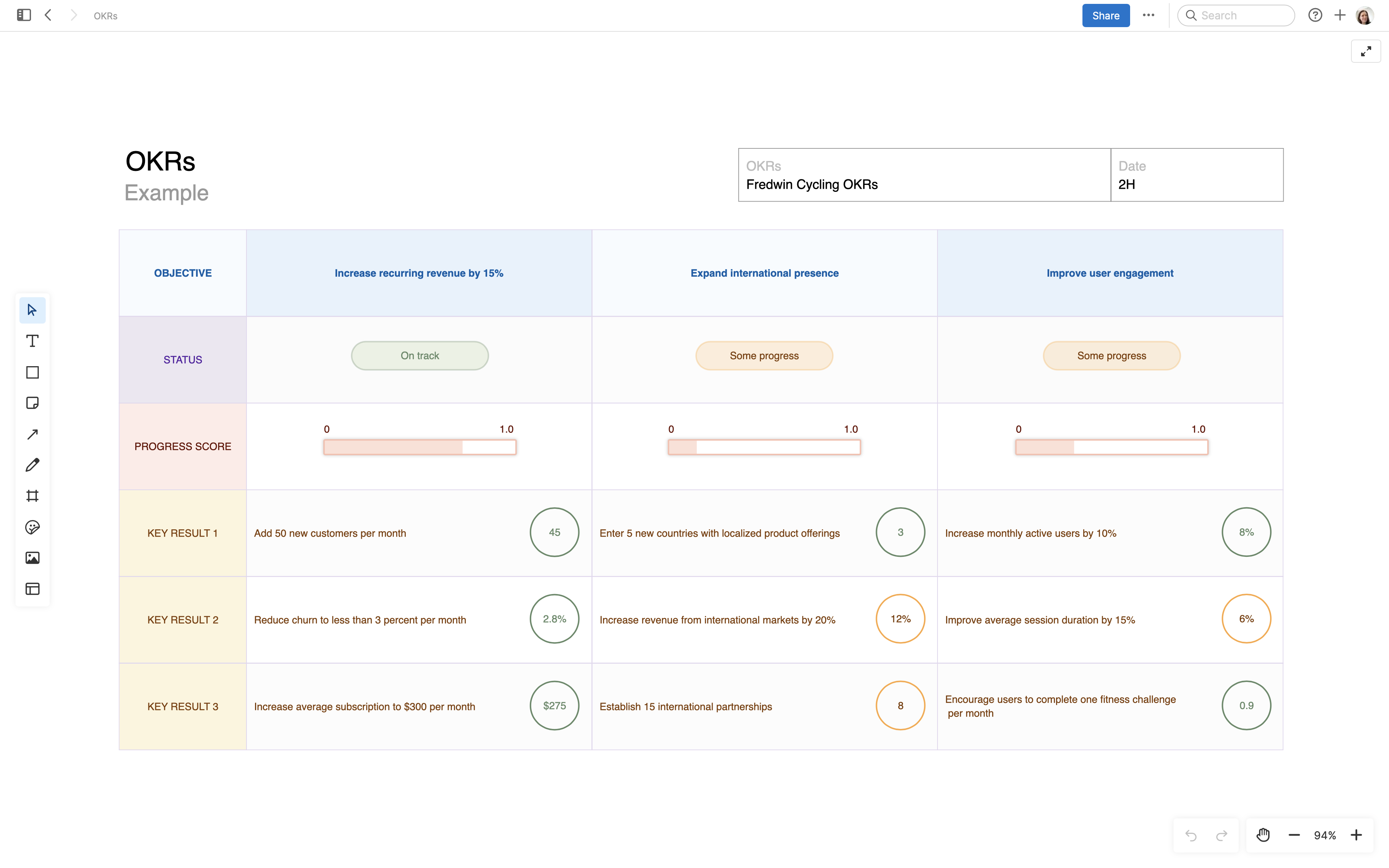
In this guide, we will share resources for three key areas — IT assessments, IT SWOT analysis, and IT strategy — along with some best practices. Together, these tools and templates will help you evaluate your current infrastructure and identify strategic opportunities to improve.
Manage strategic IT initiatives — try Aha! software.
Let's dive in. Read on or jump ahead here:
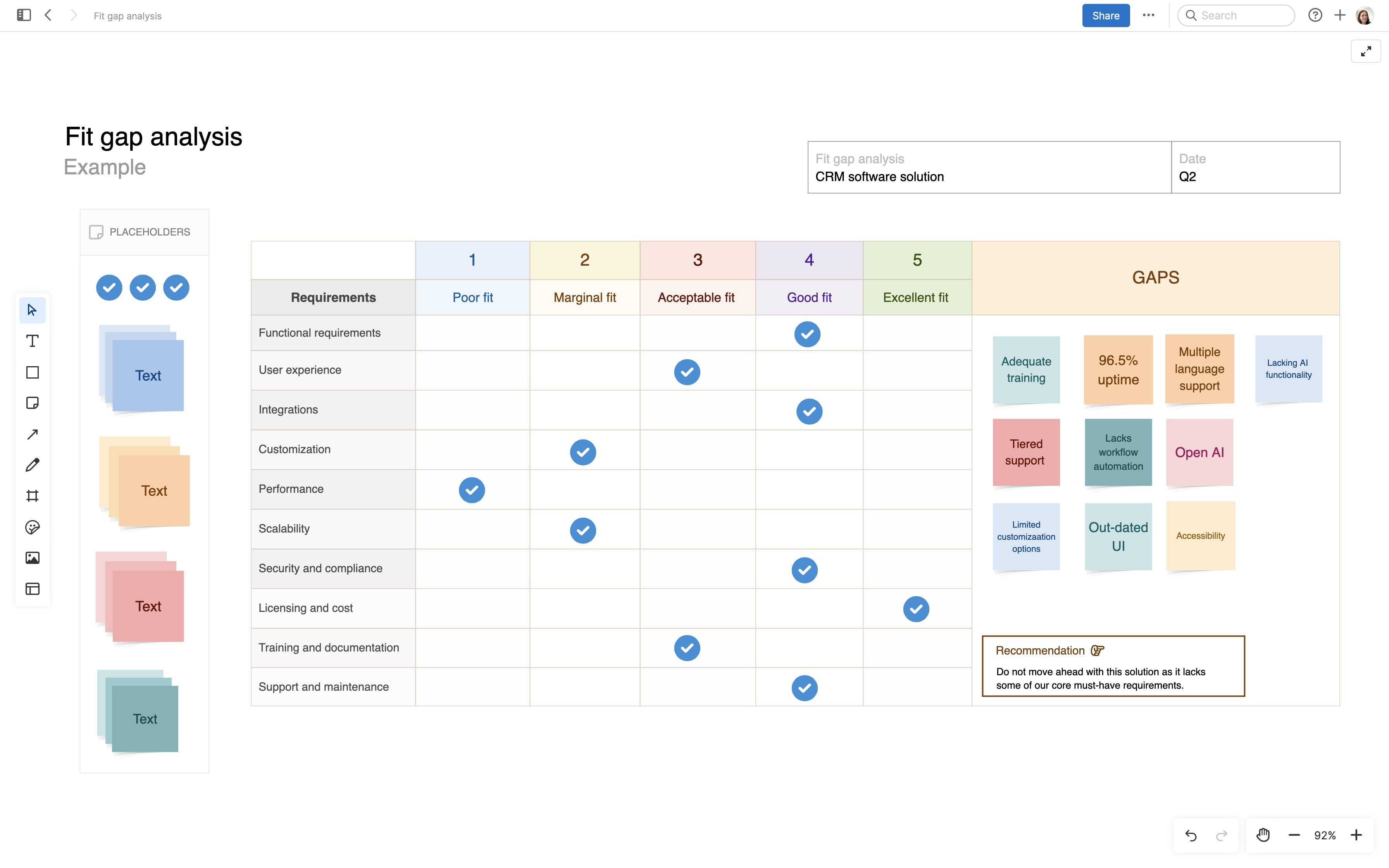
What is an IT assessment?
An IT assessment is the formal process of analyzing all the data, systems, and procedures in your IT environment. It helps you evaluate the state of your infrastructure today — making it easier to identify critical areas to improve (such as outdated tools or missing policies). Most importantly, it gives you a clear view of where improvements are needed so you can prioritize and plan accordingly.
Many IT teams conduct IT assessments annually or biannually. Be sure to also reassess after any "triggering event," or something that could potentially disrupt or compromise systems and policies. A triggering event could include:
Embarking on an enterprise transformation
Migrating legacy systems to the cloud
Moving a data center
Opening or relocating to a new office space
Using an IT assessment checklist, or IT infrastructure checklist, helps you be thorough in this process. As a plus, review periods are smoother when you have a checklist as a guide.
What to include in an IT assessment checklist
Your IT assessment checklist should cover the key systems, tools, and processes your team manages — with a focus on performance, reliability, and risk. You will also want to review prior IT assessments and documentation for any issues that have not yet been resolved.
Use this example IT assessment checklist as a starting point:
IT strategy and performance |
|
Data and cloud storage |
|
Hardware and software capabilities and inventory |
|
System maintenance |
|
Risk management and compliance |
|
Workflows and other procedures |
|
You will want to customize your own checklist to your organization, industry, and unique needs. Once you do, the next step is to develop an action plan for addressing areas of need.